Biclique cryptanalysis, introduced first in 20111 for hash cryptanalysis. After that, Bogdanove in2 used this technique and introduced the first biclique attack on full round AES. We can see lots of cryptanalysis results on the other block cipher, such as IDEA, Piccolo, LBlock, SQUARE, KLINE, ARIA, TWINE and HIGHT where proposed.3–10
Biclique attack is a kind of meet in the middle (MITM) attack that is improved for cryptanalysis block cipher to find the unknown secret key.In a biclique attack; first, all possible secret keys are partitioned into a set of groups of keys. For each group of keys, a bipartite graph is constructed. After that, a partial matching is used to filter the wrong key and get the candidate key for the correct keys .Finally, the valid pair (p,c) is used to get the correct key.
PRESENT has a simple structure and belong to a family of light weight 64-bit block cipher proposed in 2007.11 It supports two key sizes of 80 and 128 bits and denoted by PRESENT-80 and PRESENT-128. A number of biclique attacks on full round PRESENT have been published in.12–14 In this paper, we use an asymmetric independent biclique attack on full round PRESENT to reduce the data complexity. The data complexity for a full round attack on PRESENT-80 and PRESENT-128 are 217 plaintext-ciphertext pairs. By minimizing the number of active sboxes, the computational complexity is slightly improved. A summary of previous works and our result is given in Table 1.
Description of PRESENT
PRESENT is a 64-bit lightweight cipher that consists of 31 rounds with 80 or 128 bits secret key. After the final round, the state is added to XORed with round key to generate the ciphertext. Both versions of PRESENT, have the same structure as shown in Figure 1. But the key schedule is slightly different. See11for detail description of round function. The key schedule expands a secret key 80 or 128 bits to 32 round keys
with 64 bits each. In PRESENT-80, the 80 bits secret key
, is stored in 80 bits register
with
. After that, SK is updated as follow:
=
The 64 leftmost bits of SK selected as 64 bits round keys
for PRESENT-80. The above procedure is repeated until all round keys are constructed. The key schedule of PRESENT-128 is similar and is as follow
>
The above procedure is repeated, and 64 bits round keys
for PRESENT-128 are constructed as 64 leftmost bits of SK.
Biclique cryptanalysis
In this section, we give a brief overview on biclique cryptanalysis. See2 for complete detail of this. In a biclique attack, the biclique can be constructed in plaintext or ciphertext side. Here, we construct a biclique in ciphertext side so the attack is a chosen ciphertext attack, and we need the decryption oracle (for the biclique in plaintext side, the attack is a chosen plaintext attack, and we need the encryption oracle).15–18
(d1, d2) -dimensional asymmetric biclique: let f be subciher of cipher E that maps an intermediate state S to the ciphertext
. The
is called
-dimensional asymmetric biclique if for all
and
. The structure (d1, d2) -dimensional asymmetric biclique is shown in Figure 2.
The four main steps of the biclique attack are:
Key partitioning: An adversary chooses a partition of the key space into groups of key of cardinality 2(d1+d2) each. A key in a group is indexed as an element of 2d1×2d2 matrixes
Constructing a biclique: Independent biclique is an efficient tool for making a biclique. The procedure of constructing the biclique is as follow:
- Choose a random ciphertext c0 and compute
as
- Compute
as
for
- Compute
as
for
.
Partial matching: Partial matching is an efficient way that all keys in a group are tested. By using this method the computational complexity is reduced significantly. Since the biclique is constructed in the ciphertext side, partial matching is performed at the plaintext side. The remaining parts of cipher E are split into the subcipher
and
,
. We choose the matching variable after subcipher before
subcipher
The value of matching variable
is calculated in both directions to find the correct key. First, we called on the decryption oracle to obtain plaintext
. In forward direction,
is partially encrypted under key
to get
,
and stored
values. After that, in backward direction, is partially decrypted under key
to get,
and store
values. For checking the matching,, we recomputed only those parts that differ from the stored values. Note that by using partial matching, we can reduce the computational complexity significantly.
Rechecking the candidate keys: Since some candidate keys remain in each group of keys, to filter the wrong keys, the valid pair
is used to get the correct key. The structure of (d1, d2) -dimensional asymmetric biclique cryptanalysis is shown in Figure 3.
Independent asymmetric biclique attack on full round PRESENT-80
In this section, we first construct a
-dimension asymmetric biclique on the ciphertext side for round 29-31 of PRESENT-80. The partial secret key used in RK28, RK29, RK30 and RK31 are as fallow
.
.
The attack consist of four steps:
Key partitioning: The 80 bits key space is partitioned into 276 groups of
keys each. The base keys
take all 80 bits of the secret key with 4 bits fixed to zero and the remaining 76 bits take all possible values. In our attack, the differences
are chosen by varying k52 in forward direction, and the key differences
are chosen by varying
in backward direction
Constructing a biclique: We use these steps to construct a biclique for each group of keys in the ciphertext side. Let f be subcipher for round 29-31 of PRESENT-80.
Step1. Fix
and compute
Step2. Decrypt
under different keys
to get corresponding states, .The active sboxes are visualized by the blue trail in backward direction in Figure 4. These sboxes should be calculated 23 times, while the other ones are computed only once; already done in step1.
Step3. Encrypt s0 under key
to get the corresponding state c1. The active sboxes are visualized by the red trail in forward direction in Figure 5. These sboxes should be calculated 2 times, while the other ones have already been computed.
Matching: We use partial matching by applying matching with precomputation and recomputation over the remaining round of the cipher to filter the wrong key. Let
and
be subciphers for rounds 1-15 and rounds 16-28 respectively. We take matching variable v in the bits
of the state
after round 15. Then we detect the right key by computing v in both directions. The correct key is the one that meets in both directions.
Complexity
The cost of a biclique is dominated by the number of sboxes to be calculated, so we count the number of sbox operations in the round transformation and key schedule. Each round of PRESENT-80 together with one round of key schedule takes 17 sbox computations, so the complexity of single encryption equals calculation of
sboxes.
Biclique complexity: For each 276 groups of keys, the following computations should be calculated.
Forward direction complexity: In forward direction, 5 sboxes should be calculated 2 times. The active sboxes are visualized by the red trail in forward direction in Figure 4.
Backward direction complexity: In backward direction, 17 sboxes should be calculated23=8 times. The active sboxes are visualized by the blue trail in backward direction in Figure 4.The remaining 26 sboxes are calculated once. In total,
sboxes should be calculated to construct a biclique.
Matching complexity: For each276 groups of keys the following computations should be calculated.
Forward direction complexity: In forward direction,
sboxes in round transformation and 2 sboxes in key schedule should be calculated 23 times, and 25 sboxes are calculated only once. The active sboxes are visualized by the blue trail in forward direction in Figure 5. Note that 12 sboxes in round 15 need not to be computated. This procedure is repeated 2 times for all
's, so in forward direction,
ssboxes should be calculated.
Backward direction complexity: In backward direction, 42 sboxes are calculated once,
and sboxes in round transformation and one sbox in key schedule should be calculated 2 times. The active sboxes are visualized by the red trail in backward direction in Figure 5. This procedure is repeated 23 for all sj's, so in backward direction,
sboxes should be calculated.
Rechecking the candidate keys complexity: Since in each group, 24 keys should be checked and the probability of matching is 2-4, so
remaining key candidate should be tested to get the correct key.
In total, the computational complexity of our attack is given by:
Data complexity: We need at most 217 chosen ciphertexts for performing a biclique attack.
Independent asymmetric biclique attack on full round PRESENT-128: In this section, we describe our attack on PRESENT-128. Since a biclique attack on full round PRESENT-128 is similar to PRESENT-80, we only state our results.
The partial keys used in RK27, RK28, RK29, RK30 and RK31 are as fallow:
RK27:
RK28:
RK29
RK30:
RK31:
We construct (1, 3)-dimensional asymmetric biclique on the ciphertext side for round 27-31. The key differences
are chosen by varying k19 in forward direction and the key differences
are chosen by varying
in backward direction. The biclique construction is illustrated in Figure 6. Here, f, g1 and g2 are subciphers for rounds 28-31, rounds 1-14 and rounds 15-27 respectively. As we see, the
affects only 17 bits of ciphertext, and since we use the same value for c0 in each biclique, the data complexity does not exceed 217. We take matching variable v; the least significant 4 bits of the output value after round 14 as shown in Figure 7.
Complexity
Each round of PRESENT-128 together with one round of key schedule takes 18 sbox computations, so the complexity of single encryption equals calculation of
sboxes. The complexity of our attack is given by:
Biclique complexity: In forward direction, 5 sboxes in round transformation and one sbox in key schedule should be calculated 2 times. The active sboxes are visualized by the red trail in forward direction in Figure 6. In backward direction, 15 sboxes should be calculated 23=8 times. The active sboxes are visualized by the blue trail in backward direction in Figure 6. The remaining 44 sboxes are calculated once. In total
sboxes should be calculated to construct a biclique.
Matching complexity: In forward direction,
sboxes in round transformation and one sbox in key schedule should be calculated
times and 26 sboxes are calculated once only. The active sboxes are visualized by the blue trail in forward direction in Figure 7. This procedure is repeated 2 times for all
's, so in forward direction
, sboxes should be calculated. In backward direction, 43 sboxes are calculated once and
sboxes in round transformation should be calculated 2 times. The active sboxes are visualized by the red trail in backward direction in Figure 7. This procedure is repeated 23 times for all
's, so in backward direction,
sboxes should be calculated.
Rechecking the candidate keys complexity: Since in each group, 24 keys should be checked and the probability of matching is 2-4, so
remaining key candidate should be tested to reach the correct key.
In total, the computational complexity of our attack is given by:
Data complexity: We need at most 217 chosen ciphertexts for performing a biclique attack.
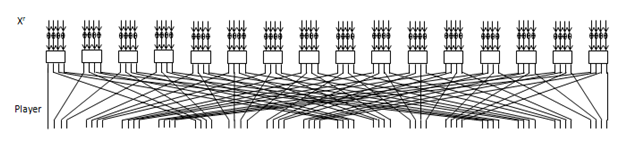
Figure 1 round function of Present.

Figure2
dimensional asymmetric biclique in the ciphertext side.

Figure 3 Representation of
-dimensional asymmetric biclique cryptanalysis.

Figure 4 3-round (1,3)-asymmetric biclique for Present-80.
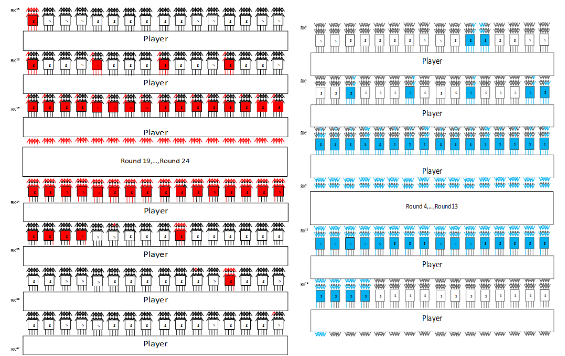
Figure 5 Recompilation in forward and backward direction for Present-80.

Figure 6 4-round (1,3)-asymmetric biclique for Present-128.
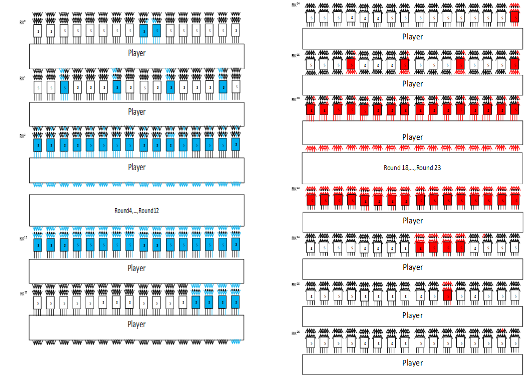
Figure 7 Recompilation in forward and backward direction for Present-128.
Version |
Round |
Computation |
Data |
Reference |
PRESENT-80 |
full |
279.76 |
223 |
15 |
|
full |
279.49 |
225 |
16 |
|
full |
279.86 |
223 |
17 |
|
full |
279.64 |
217 |
This attack |
PRESENT-128 |
full |
2127.81 |
219 |
15 |
|
full |
2127.32 |
223 |
16 |
|
full |
2127.91 |
219 |
17 |
|
full |
2127.5 |
217 |
This attack |
Table 1 Summary of biclique cryptanalytic results on PRESENT
Outline: First in section 2, the structure of PRESENT is described. We overview biclique cryptanalysis in section3.
Section 4 contains a detailed description of our attack and compute complexity.
Finally, we conclude our work in section 5.


