International Journal of
eISSN: 2573-2838


Research Article Volume 2 Issue 1
1University of Enna Kore, Italy
2Institute of Molecular Bioimaging and Physiology, Italy
3Department of Biopathology and Medical Biotechnologies, University of Palermo, Italy
Correspondence: Vincenzo Conti, Faculty of Engineering and Architecture, University of Enna Kore, Viale delle Olimpiadi, 94100 Enna, Italy
Received: December 27, 2016 | Published: January 26, 2017
Citation: Conti V, Militello C, Vitabile S. Biometric authentication overview: a fingerprint recognition sensor description. Int J Biosen Bioelectron. 2017;2(1):26–31. DOI: 10.15406/ijbsbe.2017.02.00011
Biometrics provides an alternative paradigm for the personal authentication: our biological characteristics are unique and can be used to distinguish us from the other persons. Biometrics are automated methods of identifying a person or verifying the identity of a person based on a physiological or behavioral characteristic. Examples of physiological characteristics include hand or finger images, facial characteristics, and iris recognition. Behavioral characteristics are traits that are learned or acquired. Dynamic signature verification, speaker verification, and keystroke dynamics are examples of behavioral characteristics. In this paper a general overview of biometric systems based on the principal biometric technologies available and a description of a fingerprint recognition sensor performances are proposed. To test the biometric sensor performances two indexes are used, FAR (false accept rate) and FRR (false reject rate).
Keywords: sensor, biometric technologies, user security, recognition systems
FAR, false accept rate; FRR, false reject rate; EER, equal error rate; ROC, receiver operating characteristic
Today, the actual technological scenario provides advanced services to the user, neglecting a very important factor: the security. For example, it is necessary to remember a lot of passwords to access into our online banking account, or into our email box, ecc.1 The standard authentication systems, based on username and password, are not able to assure a suitable protection level for the transmitted information. This authentication mechanism unfortunately is not sure: whoever can illegitimately know and reproduce the secret information that should guarantee only our access. The security user should be the main point of any software application dealing with personal information. The biometric science provides an alternative paradigm for the personal authentication: our biological characteristics are unique and can be used to distinguish us from the others person.2
In this paper a general overview of biometric systems and of the principal biometric technologies available is proposed and two indexes, FAR (false accept rate) and FRR (false reject rate), have been used to test the described fingerprint recognition sensor performances. The paper is organized as follow: in the section 2 are illustrated the possible modalities to user authenticate, considering the security issues related the biometric identity management; in the section 3 the principal functionalities and characteristics of a biometric system are analyzed, considering usability and problems; the section 4 introduces a set of existent available biometric technologies; in the section 5 the performance achievable from various biometric technologies are reported and finally some conclusions are reported.
In every authentication system, each user can use a service only if the following two security phases are performed
The authentication of the user digital identity is classified in the three following approach3
Something that one knows: if the user knows a pre-determined secret (generally represented by a password) then he is the correct person. In this system, the access is strongly conditioned by the password location: the probability that an impostor knows the password is high. This approach is called knowledge-based, because it uses information that only the user know.
Something that one has: if a user possesses a pre-arranged token (magnetic badge or smartcard) then he is the correct person. The token proprietary should have full access, without asking other additional information. Also here, the access to the system, and therefore its safety state, is strongly conditioned by the token location. This approach is called token-based, because it uses information that the user possesses.
Something that one is: in this approach, the concept is that the system compares user biometric characteristics with pre-registered values, known as template, allowing the access only if the measured characteristic corresponds to template stored in the system.
The more common authentication systems use the first and the second approach (or a their combination) to realize the user recognition. These kind of systems can be easily violated, simply stealing the token or knowing the password. These two approaches require that the user remember or carries with him “something” containing the necessary information for the authentication. With the third approach instead, the user haven’t the necessity to remember or to carry with him nothing: all information necessary for authentication belong to the user. User physical and behavioral characteristics (as the face geometry, the iris and retina scansion, the fingerprints, the voice, the calligraphy and so on) constitute the core of biometric systems. The biometric identity has the advantage to assure that only the correct user can have access to determined services: only who presents the correct physical characteristics will have guaranteed the access. A biometric system is based on a biometric characteristic, that cannot be stolen, and for this it is not easily violable. For example, if a smartcard containing the biometric template is stolen, nobody will can utilize it because its biometric data will not coincide with those stored on the smartcard. The system access will be denied.3
A biometric system, using the digital technologies, can be used in two different ways
Identification mode: the user is identified by a database of people known to the system (who am I?).
Authentication mode: The users declare his identity and the system verifies it (I am who say I am?).
A biometric system constitutes an automatic device for identification or authentication of the personal identity using its biological characteristics. The database, containing an digital representation (template) of the biometric characteristic, can be centralized or distributed. If the database is distributed, every user will possess a personal support, as a smartcard with own biometrics characteristics.3
In a authentication system, two different phases are performed
Enrollment phase: it is performed to insert the biometric characteristic in the system database. During this phase three specific operations are performed: biometric characteristic acquisition, digital biometric representation extraction and template storing in the database.
Verification phase: it is effected every time that a user must be authenticated for accessing the system. Three operations are effected: biometric characteristic acquisition, biometric digital representation extraction, matching between the online acquisition biometric characteristics and the templates previously created in the enrollment phase.
Performance evaluation indexes
The biometric system performances can be valued considering the following main values:
The template dimension, using smartcard for storage, is a principal issue in the selection of the biometric technologies type. The time employed by the system to take a decision is fundamental, especially in real-time applications. The recognition accuracy is the most important characteristics of the biometric recognition systems because it determines the system security.4 The recognition performance is valued using two error indexes: the FAR, percentage of approved impostors, and the FRR, percentage of refused registered user. These two percentages are always calculated: for every FAR there is a relative FRR (Figure 1).

In a ideal biometric system these percentages would be both zero. Unfortunately, the ideal system doesn't exist and therefore it will need to choose a compromise among the FAR and FRR values: the common applications try to hold lower possible these two indexes. To evaluate the global percentage of error of the system is used the EER (Equal Error Rate), defined as the percentage when the FAR and FRR are equal. With biometry must be defined a metric to establish the closeness of the comparison with a value of cut-off: only if the value associated to the biometric characteristic measured overcomes the cut-off value, then the system will recognize the user identity. Naturally, the system administrator, when establish a cut-off value, chooses a compromise (trade-off) among the probability of false acceptances (allowing the access the wrong person) and of false rejections (denying the access to the correct person). The (Figure 2) illustrates an example of some thresholds to establish the matching closeness of the biometric systems and the relative compromise among the indexes FAR and FRR.
The (Figure 2A) shows two possible values distributions of closeness among user (continuous curve) and impostor (dashed curve). For any threshold chosen, sometimes will be true user refused and impostor accepted. Particularly, the false acceptances are to the right of the dashed curve and the false rejections are to the left of the continuous curve. In these systems to improve the accuracy, the area under the user distribution will increase and the area under the impostor curve will decrease. The (Figure 2B) illustrates the FAR versus the FRR, known as ROC (Receiver Operating Characteristic) varying the considered thresholds (A, B and C). A better accuracy of the biometric system reduces the space under this curve.
Biometric characteristics usability
The following Table 1 shows the more common human physiological and behavioral characteristics used to implement a biometric system.
Biometric Technology |
Universally |
Distinctiveness |
Permanence |
Performance |
Acceptability |
Face Geometry |
High |
Low |
Medium |
Low |
High |
Facial Thermogram |
High |
Low |
Medium |
Low |
High |
Fingerprint |
Medium |
High |
High |
High |
Medium |
Hand Geometry |
Medium |
Medium |
Medium |
Medium |
Medium |
Iris |
High |
High |
High |
High |
Low |
Retina |
High |
High |
Medium |
High |
Low |
Voice |
Medium |
Low |
Low |
Low |
High |
Calligraphy |
Low |
Low |
Low |
Low |
High |
Table 1 Comparison between biometric technologies
These characteristics possess the following specific property3
In this section, the principal biometric technologies are illustrated. Each technology has advantages and disadvantages, in fact, don't exist an all-purpose correct technology for every system.5 In the following (Figure 3), a classification of the most common biometric characteristics is given.
Face geometry and facial thermo gram
The biometric systems using facial recognition6,7 are based on the distance among facial attributes (i.e. the distance among the eyes) and on their shape (i.e. the mouth ampleness). In the system access phase a face image is acquired and provided to the system to compare it with the image stored in the database (Figure 4A). This technology has a good impact on the user, since it is less intrusive and it is not expensive. Facial geometry recognition approach is very sensitive to the variations in the illumination, to the different face positions and expressions.
The performances decrease when the dimension of the database increases (the twins are hardly distinguishable). The facial thermo gram8 is based on the model of the blood vases and on the temperature of many face points (Figure 4B). Unfortunately facial thermo gram is sensitive to the emotional state and to the health state of the person.
Fingerprint recognition
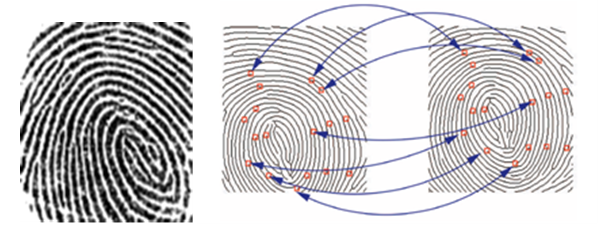
The fingerprints are unique, don't change in the time and are different also in identical twins (Figure 5). Also this technology has some limits: excessively damp or dry skin can compromise the systems performances, sometimes fingerprints are not usable because of cuts or scars, besides they have an ugly impact on the user, for the association that is done between the figure of the criminal and the fingerprints. Such technology is the more common even if it is not easy to be implemented for big computational cost and request resources.9,10
Hand geometry
The form and the dimensions of the hand can be used as distinctive characteristics 11. The hand geometry recognition systems (Figure 6A) have many advantages respect the fingerprints: it requires less space to store the templates, the whole system is more convenient and meets small psychological resistance from humans. But also this technology has some defects: the people don't want to put the palm where many other have put theirs. The performances depend from the weather conditions or from the hand cleanness and the form of the hand is not invariant during the life. Finally, a real problem is the big dimension of the hand sensor (Figure 6B), so this technology is not appropriate for some applications, how portable devices (cellular, pod and so on).
Iris scansion
The iris scanning recognition12,13 is based on the iris characteristics of the human eye (Figure 7B). After the DNA, the iris is the biometric characteristic more discriminating of the human body: also the identical twins have different iris. This technology uses particular video cameras for the scanning and is not necessary a contact between the eye of the subject and the biometric scanner (Figure 7A). The iris is less susceptible to damage respect to other parts of the body, the template asks only few byte for storage and the system works even if the person is carrying glasses.
Calligraphy recognition
This technique is based on the characteristic that every person has an unique style to write. A problem is that two writings of the same person are not never perfectly identical. This implicates a mediocrity reliability that brings this technology to be used only on small target of population. Two approaches exist for the calligraphy recognition: static and dynamic.14 The dynamic method uses also acceleration, speed and pressure of the person that is writing for improving the recognition accuracy.
Retina scansion
The veins conformation under the retina surface of the eye is unique and therefore it is a characteristic usable for personal recognition.15,16 The retina scanning is affected sending a beam of low intensity light inside the ocular bulb and storing the pattern constituted by the eye veins (Figure 8). The user has to be near the scanner and to focus a specific point with own eye: this type of system is less attractive. Besides the sensors are still rather expensive and the retina veins distribution changes during the human life.
Voice recognition
The voice recognition is considered the least accurate technology,17 but it is preferred from the users and can provide the secure access to information through the telephone lines (Figure 9). The voice recognition can be text-dependent or text-independent: in the first case, the user says a predetermined sentence; in the second case (less accurate) the user simply says something.
The problem of this technology is that the user can realize a great variety of voice inflexions for environment variations or for stress. The environmental noises can strongly reduce the performances. The twins and the brothers are hardly distinguishable; also among different people the error percentages are high. This technology doesn't realize recognition on wide scale.
Choice of biometric technology
The biometric technologies guarantees the secure user recognition in different field, that mainly regard:1,4,5
The physical accesses control: it concerns those areas where it is important to recognize who enters and who go out (for example in the offices, hospitals, jails, etc...).
The logical accesses control: it concerns the access through computer nets, cellular telephones, sets electronics to reserved data or services where security is important (e-banking, e-mail and so on).
The choice of biometric technology is usually done by the following factors:
The Table 2 shows some of the principal characteristics of the proposed technologies.
Biometric Technology |
Frr Range (%) |
Far Range (%) |
Cost |
Template Dimension (Bytes) |
User Acceptance |
Face Geometry |
10÷20 |
0.001÷1 |
Medium |
Few bytes |
High |
Hand Geometry |
1÷10 |
1 |
Medium |
<10 |
Medium |
Iris Scansion |
1÷10 |
~0 |
High |
512 |
Low |
Retina Scansion |
1 |
0.01 |
Very High |
Low |
|
Voice |
10÷20 |
2÷5 |
Low |
1500 |
High |
Calligraphy |
3÷10 |
1 |
Medium |
1500 |
High |
Fingerprint |
3÷7 |
0.0001÷0.001 |
Medium |
300÷1200 |
Medium |
Table 2 Comparison between biometric technologies
In this section a fingerprints authentication system is described.18-20 This biometric sensor is composed of three modules: UIM, PM and AM (Figure 10).
UIM: user interface module
The UIM is a module expressly developed for providing the necessary interface to the user for access to the enrolment and authentication functionalities, provided by the biometric sensor. During the phase of enrolment, the followings steps can be individualized:
Instead, in the phase authentication, it is possible to individualize the following steps:
PM: processing module
The PM is a module that implements all the elaborations necessary to extract from fingerprints the biometric template. Are realised the followings six tasks: normalization, binarization, thinning, minutiae extraction, digital template encryption/decryption and matching.21,22
AM: acquisition module
The AM manages the fingerprint scanner and the fingerprint capture. It is constituted by the device Precise Biometrics PB100MC and from the BSP (Biometric Service Provider) provided by the Bio APIs.23,24 Inside the standard interface provided by the Bio APIs, the basic model of operation is the same, independently from the biometric technology used. First of all a user template must be created. The characteristics extracted by the samples, will go to constitute the template that will be memorized by the biometric system.
Recognitions analysis
The biometric system performance has been effected through the FAR and FRR percentages. An ideal authentication sensor would have FAR and FRR values equal to zero, instead, in a real system, users regularly recorded are refused by the system (false rejections) and users non-recorded are accepted (false acceptances). Thus the values of FAR and FRR are not zero. Naturally more lower are these values and best will be the recognition efficiency. For the evaluation of these index and for their optimal choice, different tests have been effected on a set of 352 fingerprints of 88 users captured through the fingerprint scanned PB100MC.
Sensor Performance |
Minutiae Used For Matching |
|||||||||
|---|---|---|---|---|---|---|---|---|---|---|
85% |
90% |
93% |
95% |
97% |
||||||
Fingerprints Number |
FAR (%) |
FRR (%) |
FAR (%) |
FRR (%) |
FAR (%) |
FRR (%) |
FAR (%) |
FRR (%) |
FAR (%) |
FRR (%) |
2 |
6,35 |
3,13 |
2,99 |
5,21 |
1,68 |
7,29 |
1,07 |
8,33 |
0,98 |
11,46 |
3 |
3,93 |
8,33 |
1,71 |
14,58 |
1,12 |
17,71 |
0,78 |
22,92 |
0,71 |
26,04 |
4 |
2,16 |
25,00 |
0,99 |
32,29 |
0,87 |
40,63 |
0,60 |
46,88 |
0,41 |
52,08 |
Table 3 FAR and FRR values considering a variable minimum percentage of minutiae matched and 2, 3 and 4 fingerprint to authenticate user
Biometry allows the automatic user authentication sensor using his physiological or behavioral characteristics increasing the system security level. The biometric sensor constitute a valid alternative respect the “conventional” authentication systems, based on traditional authentication methods (like password and PIN). The modern biometric sensors are less expensive and also more miniaturized and this allows an easier diffusion of biometric authentication systems. Besides the biometry is an effective strategy for the privacy protection. Finally, biometric sensors, in the future, will can be used in almost every transaction that needs secure personal authentication.
None.
The author declares no conflict of interest.

©2017 Conti, et al. This is an open access article distributed under the terms of the, which permits unrestricted use, distribution, and build upon your work non-commercially.